 The Lockbox Story: How Alice and Bob Keep Secrets Safe
The Lockbox Story: How Alice and Bob Keep Secrets Safe
Once upon a time in the digital world, two friends—Alice and Bob—wanted to exchange secret messages. But there was a problem: the internet is like a giant, open highway. Anyone could intercept their messages if they weren’t careful.
So, they came up with a clever plan. And it all started with a padlock.
Sending Secrets: Bob’s Love Letter to Alice
Bob had something special to say to Alice—a heartfelt love letter. But he couldn’t just send it over the internet. What if someone snooped?
 Luckily, Alice had a solution. She handed Bob an open padlock. This wasn’t any ordinary lock—it was one that only she had the key to. In the world of encryption, this open padlock is called a public key. Anyone can use it to lock a message, but only the person with the private key can unlock it.
Luckily, Alice had a solution. She handed Bob an open padlock. This wasn’t any ordinary lock—it was one that only she had the key to. In the world of encryption, this open padlock is called a public key. Anyone can use it to lock a message, but only the person with the private key can unlock it.
Public Key = Open padlock you can share with anyone.
Private Key = The only key that can unlock that padlock.
Bob placed his love letter in a box, locked it using Alice’s public key, and sent it on its way. Even he couldn’t open it again! Only Alice had the matching private key to unlock the box.
Receiving Secrets: Alice Unlocks the Message
When Alice received the locked box, she simply used her private key to open it and read Bob’s message.
No one else could have done that—not even Bob—because only Alice had the unique key that matched the lock. That’s the magic of asymmetric encryption: one key to lock, another to unlock.
🛡️ But Wait—What if Someone Swaps the Lock?
Before any of this could happen, Bob needed to be sure the padlock was really from Alice. What if a hacker gave him a fake lock and read all the messages?
This is where public key verification comes into play.
Option 1: Certificate Authorities (CA)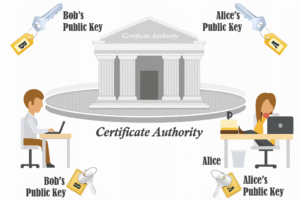
Alice registers her public key with a trusted organization called a Certificate Authority. When Bob receives the key, his browser checks with the CA to confirm it’s legit.
Think of it like Alice giving Bob her lock, along with a stamped letter from a notary confirming it’s hers.
This is how SSL/TLS certificates work on websites. When you visit a secure site like https://google.com, your browser checks that Google’s certificate (and its public key) has been signed by a trusted CA, like DigiCert or Let’s Encrypt.
🤝 Option 2: Out-of-Band Verification
Sometimes, Bob and Alice verify keys directly. Bob might call Alice or scan a QR code to confirm the lock’s fingerprint. This is common in SSH or PGP.
Either way, the goal is the same: make sure the lock really belongs to Alice.
Note: Public keys themselves aren’t encrypted—they’re meant to be shared! But digital certificates are signed by a CA’s private key to prove authenticity.
🔁 Once Verified: Let the Secret Chat Begin
Now that Bob is sure he has the right lock, it’s time for the real magic to happen.
Step 1: Key Exchange with Asymmetric Encryption
Bob’s browser generates a random, temporary key for fast encryption (called a symmetric key), locks it with Alice’s public key, and sends it.
Only Alice can unlock it with her private key. Now both sides share the same secret key—safely.
Step 2: Fast & Secure Conversation with Symmetric Encryption
Now that they both have the same symmetric key, all further messages are encrypted with it.
Why use symmetric encryption now?
Because it’s 100x faster than asymmetric encryption!
A Real-World Example: What Happens When You Visit a Secure Website
-
You open
https://secure-website.com -
The site sends you its certificate (with the public key).
-
Your browser verifies it using a trusted CA.
-
Your browser creates a symmetric key, encrypts it with the site’s public key, and sends it.
-
The site decrypts it using its private key.
-
Now, both of you share a symmetric key. All your communication is securely encrypted.
🔄 Why Mix Two Types of Encryptions?
Because each has its strengths:
-
Asymmetric Encryption is great for secure key exchange.
-
Symmetric Encryption is ideal for fast data transfer.
Together, they form a perfect team. This hybrid approach powers the security behind HTTPS, SSH, VPNs, and many other tools we rely on every day.
Final Thought
So, the next time you see a little padlock in your browser bar, remember Alice and Bob. Behind that symbol lies a beautiful dance of cryptography—ensuring your messages, logins, and secrets stay just that: secret.

Leave a Reply