
Have you ever wondered how websites keep your information safe when you shop online or log in to your email? The answer lies in something called Public Key Infrastructure (PKI). PKI is like a digital security system that helps protect your data and verify who you’re talking to online. Let’s break it down in simple terms so anyone can understand!
What is PKI?
PKI is a system that uses special digital tools to keep online communication secure. It helps:
– Verify identities: Make sure you’re talking to the right person or website.
– Encrypt data: Scramble information so only the intended recipient can read it.
– Ensure trust: Create a safe environment for sharing sensitive information.
You encounter PKI every day when you see a little padlock icon in your browser or use HTTPS websites.
How Does PKI Work?
Think of PKI as a digital ID system. Here’s how it works step by step:
1. Create a Key Pair:
Every user or device gets two keys: a private key (like a secret password) and a public key (like a shared lock).
The private key is kept secret, while the public key can be shared with anyone.
2. Request a Digital ID (CSR):
To get a digital ID (called a certificate), you send a request (called a CSR) to a trusted authority.
This request includes your public key and some info about you (like your name or website address).
3. Get Your Digital ID (Certificate):
A trusted authority (called a Certificate Authority or CA) checks your info and gives you a digital certificate.
This certificate links your public key to your identity and has an expiration date.
4. Use Your Digital ID:
You install the certificate on your device or server.
When someone connects to you (like visiting your website), they check your certificate to make sure it’s valid and trusted.
5. Establish Trust:
If everything checks out, a secure connection is created, and your data is protected.
Key Parts of PKI
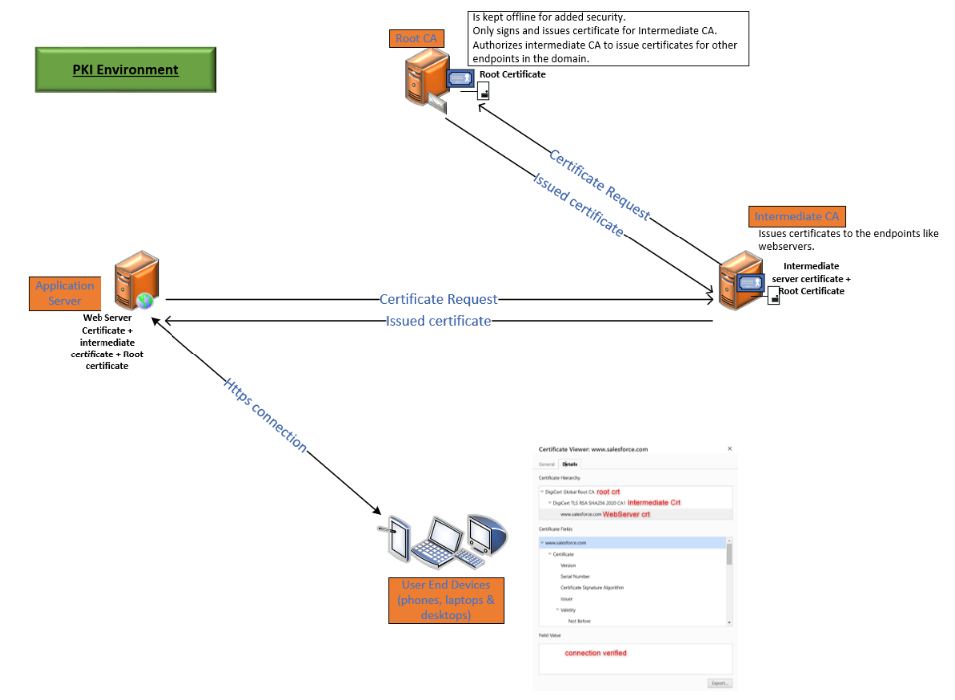
1. Root Certificate Authority (Root CA)
This is the “boss” of the PKI system. It’s super trusted and doesn’t directly issue certificates to users. Instead, it gives authority to others (called Intermediate CAs) to do that.
2. Intermediate Certificate Authority (Intermediate CA)
These are like middle managers. They issue certificates to users and devices but get their authority from the Root CA.
Using Intermediate CAs adds an extra layer of security.
3. Certificate Signing Request (CSR)
This is like filling out a form to get your digital ID. It includes your public key and some info about you.
4. Private and Public Keys
Private Key: A secret key only you have. It’s used to unlock messages or prove your identity.
Public Key: A key you share with others. It’s used to lock messages so only you can open them.
5. Digital Certificates
These are like digital IDs. They link your public key to your identity and are issued by a trusted CA.
6. Machine Certificates
These are digital IDs for devices (like servers or smart devices). They help machines securely communicate with each other.
PKI in Real Life: An Example
Imagine you’re visiting a secure website (like your bank):
1. Your browser connects to the bank’s server.
2. The server shows its digital certificate, which includes its public key.
3. Your browser checks if the certificate is valid and trusted by a public Root CA or Intermediate CA.
4. If everything’s good, your browser uses the server’s public key to encrypt your data (like your login info).
5. The server uses its private key to decrypt the data, ensuring only it can read it.
Why is PKI Important?
– Keeps Data Safe: Encrypts information so hackers can’t read it.
– Verifies Identities: Ensures you’re talking to the right person or website.
– Prevents Tampering: Makes sure no one alters your data during transmission.
– Builds Trust: Creates a secure environment for online activities.
Challenges with PKI
– Complexity: Setting up and managing PKI can be tricky.
– Expiration: Certificates need to be renewed regularly.
– Security Risks: If private keys are stolen, the system can be compromised.
Tips for Using PKI
1. Protect Private Keys: Keep them safe, like you would a password.
2. Use Intermediate CAs: Adds an extra layer of security.
3. Automate Management: Use tools to handle certificate renewals and updates.
4. Stay Updated: Keep up with the latest security practices.
Conclusion
PKI is like the invisible shield that keeps your online activities safe. Whether you’re shopping, sending emails, or logging into your accounts, PKI works behind the scenes to protect your data and verify identities. By understanding the basics—like Root CAs, Intermediate CAs, private and public keys, and digital certificates—you can better appreciate how trust and security are built into the digital world.
If you’d like to learn more about PKI or need help setting it up, feel free to explore my other blogs at [Let Me Learn](https://letmelearn.ca).

Leave a Reply